Google CTF - Ernst Echidna
Let’s talk about the Ernst Echidna web challenge of the Google CTF.
Warning: This post contains spoilers.
The challenge description goes like that:
Can you hack this website? The robots.txt sure looks interesting.
Let’s start by loading the website.
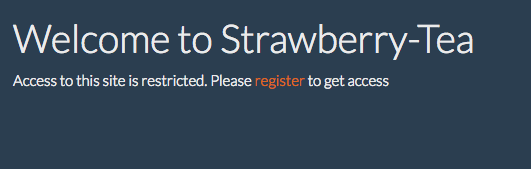
A good practice (especially on web CTF) is to follow the trails that are given, and then explore around them. Let’s follow the robots.txt trail.
Disallow: /admin
This is really informative, nothing we could have guessed. Here is the admin page:
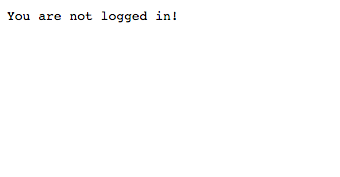
On the homepage, there is a link to register, let’s try it.
We are redirected to a welcome page that state there is no content.
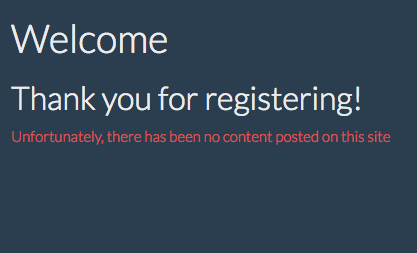
Now that we are registered (and apparently logged in), we should have a cookie to reflect that.
document.cookie; // display the cookies in the developer console
And we have a very interesting cookie:
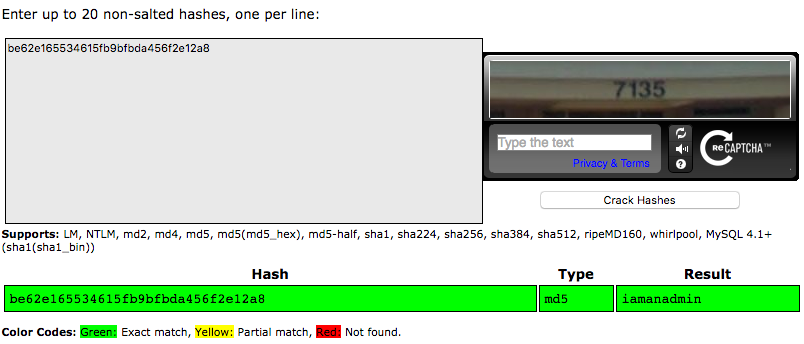
md5-hash=be62e165534615fb9bfbda456f2e12a8
It looks like it’s a md5-hash (the name is obvious, but some people are evil enough to put us on the wrong trail). I wonder what is hashed… There is a good website where you can paste a hash and it will try to match it. It will only work if the hash is not salted. The website is CrackStation
Enter your hash in the CrackStation and you should obtain your username. This is an example where it is useful to take a simple username when registering in a CTF, so that the hash is easily found.
We are logged in, and our cookie contain our username. Let’s try the admin page again.
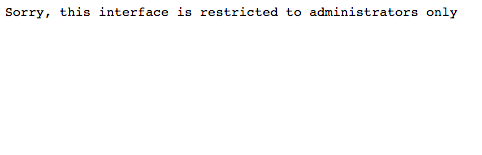
We need to become an admin. Since the token is only the md5 hash of the username, we can try to hash admin and set our cookie with the new hash. Let’s try it.
$ echo -n "admin" | md5 # Get the hash in your terminal
> 21232f297a57a5a743894a0e4a801fc3
// Set the cookie in your browser console
document.cookie = "md5-hash=21232f297a57a5a743894a0e4a801fc3";
Refresh the admin page and you have your flag!
